0) In light of the DeFi oracle attacks, I want to introduce Continuous Liquidity Pools (CLPs) - an alternative automated token exchange system.
CLPs are more resistant to atomic price manipulation attacks and can potentially serve as better on-chain price feeds
CLPs are more resistant to atomic price manipulation attacks and can potentially serve as better on-chain price feeds
1) a CLP can be thought of as "An automated market maker model with slip based fees".
This is similar to how Uniswap employs an XYK constant product AMM with fees set at 0.30%
This is similar to how Uniswap employs an XYK constant product AMM with fees set at 0.30%
2) A characteristic of Uniswap's fee model is that its pools are cheap to attack. The effect of slippage can be negated with sandwich attacks which can be executed for only 60bps.
"A sandwich attack is where an event is sandwiched by two large bi-directional trades"
"A sandwich attack is where an event is sandwiched by two large bi-directional trades"
3) Similar attacks have notably been executed against @bzxHQ, but they have actually been a problem faced by @synthetix_io for quite a while.
Synthetix has previously faced repeated price feed sandwich attacks on its arb incentive pool, forcing them to shut down the program
Synthetix has previously faced repeated price feed sandwich attacks on its arb incentive pool, forcing them to shut down the program
4) By charging a slip based fee, swaps must pay a premium based on the amount of pool liquidity they demand. CLPs bring the burden of time into decision marking and forces large actors to slow their actions down or pay large fees.
The fee equation is: x^2Y / (x+X)^2
The fee equation is: x^2Y / (x+X)^2
5) Proportional to onchain liquidity, sandwich attacks can become prohibitively expensive
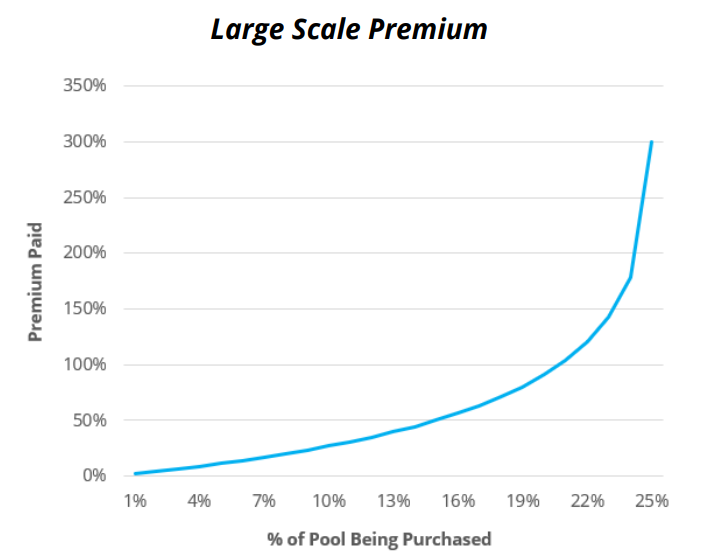
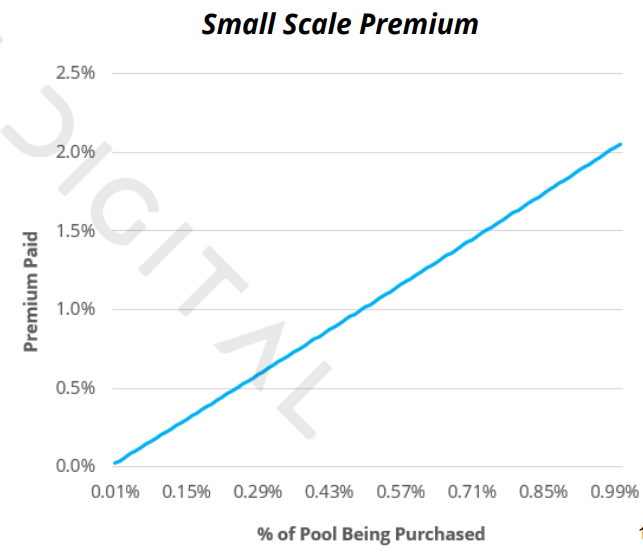
This does not necessarily mean that CLPs are more expensive for traders. See the two graphs below from @Delphi_Digital on the relationship between size of trade and premiums paid
This does not necessarily mean that CLPs are more expensive for traders. See the two graphs below from @Delphi_Digital on the relationship between size of trade and premiums paid
6) CLP does not stop all onchain price feed manipulation, but significantly increases the barrier. For example, the sUSD bZx attack could still have been profitably executed by the attacker if the same Uniswap liquidity was represented in a CLP, but at a much greater cost
7) CLPs while not yet implemented in the wild, were originally pioneered by the @thorchain_org ($RUNE) team in 2018 as part of a larger cross chain DeFi project that requires manipulation resistant onchain price feeds
8) The implications on arbitrage, impermanent loss, liquidity provisioning, etc. are quite extensive. Anyone that wishes to learn more about CLPs can review the following resources:
- https://github.com/thorchain/Resources/blob/master/Whitepapers/ASGARDEX/clp-implementation.md
- https://medium.com/thorchain/thorchains-immunity-to-impermanent-loss-8265a59066a4
- https://medium.com/thorchain/revisiting-fees-and-impermanent-loss-4fbf9ee35fd5
- https://github.com/thorchain/Resources/blob/master/Whitepapers/ASGARDEX/clp-implementation.md
- https://medium.com/thorchain/thorchains-immunity-to-impermanent-loss-8265a59066a4
- https://medium.com/thorchain/revisiting-fees-and-impermanent-loss-4fbf9ee35fd5
cc&H/T: @jpthorbjornsen @KaiAnsaari @evabeylin @YanLiberman @mediodelphi @JazearBrooks @tcbean @valentalb @CurveFinance
Note that in an Ethereum implementation of CLP, an attacker can potentially batch multiple swaps in one tx in order to circumvent the CLP fee model. This can be mitigated by limiting each address to one call per pool per block.

 Read on Twitter
Read on Twitter