Some thoughts about the #cyberattack against Australia  : facts, assessment under international law and Australia's response options.
: facts, assessment under international law and Australia's response options.
*THREAD*
/1
 : facts, assessment under international law and Australia's response options.
: facts, assessment under international law and Australia's response options. *THREAD*
/1
First, the facts:
 state actor (most likely
state actor (most likely  , but
, but  will not say)
will not say)
 persistent & ongoing campaign
persistent & ongoing campaign
 targeted are all levels of gov't, political orgs, OES and other CI operators
targeted are all levels of gov't, political orgs, OES and other CI operators
 systems were penetrated, but no info about disruptive or destructive effects
systems were penetrated, but no info about disruptive or destructive effects
/2
 state actor (most likely
state actor (most likely  , but
, but  will not say)
will not say) persistent & ongoing campaign
persistent & ongoing campaign targeted are all levels of gov't, political orgs, OES and other CI operators
targeted are all levels of gov't, political orgs, OES and other CI operators systems were penetrated, but no info about disruptive or destructive effects
systems were penetrated, but no info about disruptive or destructive effects/2
With this in mind, did this cyber operation breach international law? Let's look at:
 use of force
use of force
 non-intervention
non-intervention
 sovereignty
sovereignty
I omit due diligence, because attribution to a state actor is assumed.
/3
 use of force
use of force non-intervention
non-intervention sovereignty
sovereigntyI omit due diligence, because attribution to a state actor is assumed.
/3
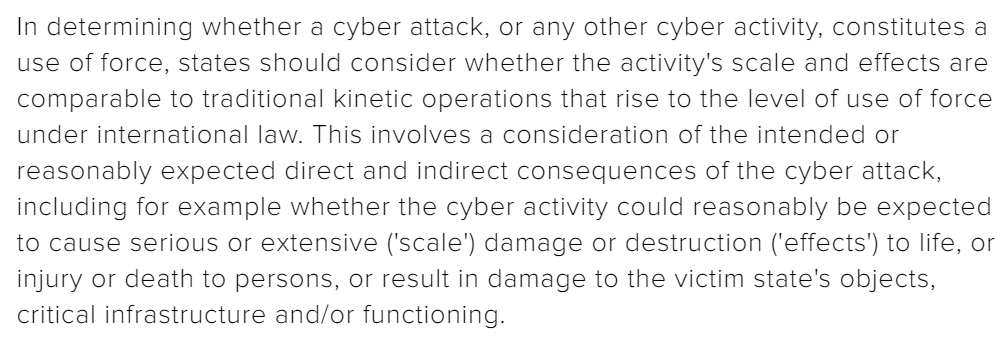
 It's fairly obvious that there has been no breach of the prohibition of the use of force. Under the scale-and-effects test, which most states (incl.
It's fairly obvious that there has been no breach of the prohibition of the use of force. Under the scale-and-effects test, which most states (incl.  ) use, a cyberattack must be comparable to kinetic operations. As no damage occured, art. 2(4) UNC is not breached.
) use, a cyberattack must be comparable to kinetic operations. As no damage occured, art. 2(4) UNC is not breached. /4
 Below-the-threshold cyberattacks can constitute a prohibited intervention into the internal affairs of another state if
Below-the-threshold cyberattacks can constitute a prohibited intervention into the internal affairs of another state if they are coercive, i.e. deprive the state of the ability to decide or act freely upon matters which
they are coercive, i.e. deprive the state of the ability to decide or act freely upon matters which fall within the domaine réservé
fall within the domaine réservé/5
Although governmental systems and critical infrastructure were affected, it seems that the actions were not coercive. Penetration of systems and exfiltration of data, without more, does not affect Australia's ability to decide freely on sovereign matters. So, no intervention.
/6
/6
 Sovereignty is more tricky. There are 3 approaches:
Sovereignty is more tricky. There are 3 approaches: sovereignty is not a rule of IL and cannot be breached by cyberattacks (
sovereignty is not a rule of IL and cannot be breached by cyberattacks ( &
& DOD)
DOD) sovereignty can be breached if there is usurpation of inherently govt functions (TM2.0&
sovereignty can be breached if there is usurpation of inherently govt functions (TM2.0& )
) penetration = breach of sovereignty (
penetration = breach of sovereignty ( )
)/7
Here,  sovereignty would only be breached under the
sovereignty would only be breached under the  approach. As there have been no reports that the penetrated systems and data thereon have been manipulated or destroyed (other than malware installation), this is not enough for usurpation of govt functions.
approach. As there have been no reports that the penetrated systems and data thereon have been manipulated or destroyed (other than malware installation), this is not enough for usurpation of govt functions.
/8
 sovereignty would only be breached under the
sovereignty would only be breached under the  approach. As there have been no reports that the penetrated systems and data thereon have been manipulated or destroyed (other than malware installation), this is not enough for usurpation of govt functions.
approach. As there have been no reports that the penetrated systems and data thereon have been manipulated or destroyed (other than malware installation), this is not enough for usurpation of govt functions./8
So far, Australia has not made its own views on sovereignty in cyberspace publicly known, so we don't know how they would assess the cyber attacks. Maybe this would be a good moment to develop a position on this issue.
/9
/9
Next, what are Australia's response options? Lets look at:
 criminal indictments
criminal indictments
 public attribution
public attribution
 sanctions
sanctions
 countermeasures
countermeasures
/10
 criminal indictments
criminal indictments public attribution
public attribution sanctions
sanctions countermeasures
countermeasures/10
 Unauthorised access to restricted data is an offence under the Australian criminal code and Australia would have territorial jurisdiction. Of course, the perpetrators would first need to be identified, but as a member of the 5 Eyes,
Unauthorised access to restricted data is an offence under the Australian criminal code and Australia would have territorial jurisdiction. Of course, the perpetrators would first need to be identified, but as a member of the 5 Eyes,  might/should have the capabilities.
might/should have the capabilities./11
 Public attribution is a sovereign political decision. Here,
Public attribution is a sovereign political decision. Here,  decided not to name the responsible state, but the political calculus might change according to the circumstances. Public attributions are not governed by IL and there is no requirement to provide evidence.
decided not to name the responsible state, but the political calculus might change according to the circumstances. Public attributions are not governed by IL and there is no requirement to provide evidence./12
 Individual sanctions or cyber restrictive measures can be qualified as retorsions and do not violate IL as long as they do not breach an international obligation owed by
Individual sanctions or cyber restrictive measures can be qualified as retorsions and do not violate IL as long as they do not breach an international obligation owed by  to the sanctioned state. Travel bans & asset freezes are the standard tools here.
to the sanctioned state. Travel bans & asset freezes are the standard tools here. /13
 Actions that affect
Actions that affect  int'l obligations towards the responsible state would constitute an internationally wrongful act and would need to be justified, most likely under the doctrine of countermeasures. For this, a previous wrongful act by the resp. state is necessary.
int'l obligations towards the responsible state would constitute an internationally wrongful act and would need to be justified, most likely under the doctrine of countermeasures. For this, a previous wrongful act by the resp. state is necessary./14
Here, only a breach of sovereignty under the French penetration-based approach would qualify. Under all other approaches, there has been no breach of sovereignty.
/15
/15
Could  hack back? IMO yes, but the justification and scope varies depending on the approach towards sovereignty.
hack back? IMO yes, but the justification and scope varies depending on the approach towards sovereignty.
Under - yes, because there is no rule of sovereignty to be breached.
- yes, because there is no rule of sovereignty to be breached.
Under - yes, provided no phys. effects or usurpation of inherently govt functions.
- yes, provided no phys. effects or usurpation of inherently govt functions.
/16
 hack back? IMO yes, but the justification and scope varies depending on the approach towards sovereignty.
hack back? IMO yes, but the justification and scope varies depending on the approach towards sovereignty.Under
 - yes, because there is no rule of sovereignty to be breached.
- yes, because there is no rule of sovereignty to be breached. Under
 - yes, provided no phys. effects or usurpation of inherently govt functions.
- yes, provided no phys. effects or usurpation of inherently govt functions. /16
Under  - yes, as a countermeasure to induce the responsible state to stop, provided proportionality and other requirements are met. Many states argue that in the cyber context, prior notification is not required if it would jeopardise the success of the countermeasure.
- yes, as a countermeasure to induce the responsible state to stop, provided proportionality and other requirements are met. Many states argue that in the cyber context, prior notification is not required if it would jeopardise the success of the countermeasure.
/17
 - yes, as a countermeasure to induce the responsible state to stop, provided proportionality and other requirements are met. Many states argue that in the cyber context, prior notification is not required if it would jeopardise the success of the countermeasure.
- yes, as a countermeasure to induce the responsible state to stop, provided proportionality and other requirements are met. Many states argue that in the cyber context, prior notification is not required if it would jeopardise the success of the countermeasure./17
And that's it. Let's see how this thing develops and how the cyber attacks will affect Australia's position on IL (esp. sovereignty) in cyberspace, if at all.
Thanks for reading! Now I'm going back to grading exams *sigh*.
All copied text from here: https://www.dfat.gov.au/publications/international-relations/international-cyber-engagement-strategy/aices/chapters/2019_international_law_supplement.html
/END
Thanks for reading! Now I'm going back to grading exams *sigh*.
All copied text from here: https://www.dfat.gov.au/publications/international-relations/international-cyber-engagement-strategy/aices/chapters/2019_international_law_supplement.html
/END
There's a typo (flagpo?) in this tweet:
Of course I meant the French approach. https://twitter.com/Roguski_P/status/1273936037652451328
Of course I meant the French approach. https://twitter.com/Roguski_P/status/1273936037652451328

 Read on Twitter
Read on Twitter