NEW RESEARCH: The attackers spreading #Conti have switched gears to a completely fileless attack method.
(a thread)
1/8
(a thread)
1/8
For the past several months, both SophosLabs and the Sophos Rapid Response team have been collaborating on detection and behavioral analysis of a ransomware that emerged last year and has undergone rapid growth.
2/8
2/8
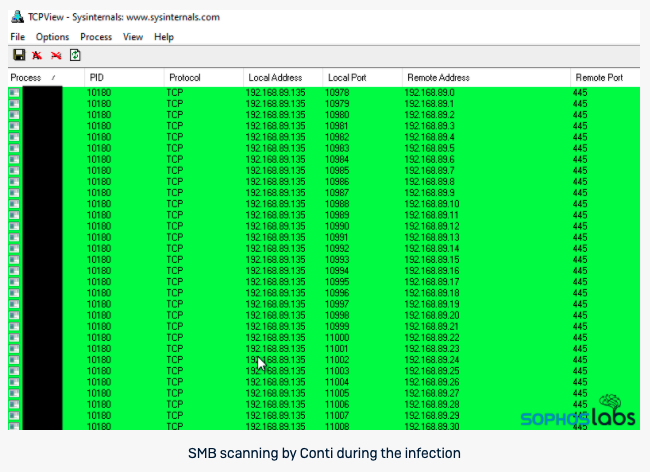
The ransomware, which calls itself #Conti, is delivered at the end of a series of Cobalt Strike/meterpreter payloads that use reflective DLL injection techniques to push the malware directly into memory.
3/8
3/8
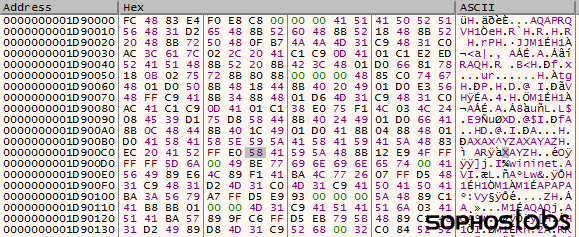
Because the reflective loaders deliver the ransomware payload into memory, never writing the ransomware binary to the infected computer's file system, the attackers eliminate a critical Achilles' heel that affects most other ransomware families...
4/8
4/8
...There is no artifact of the ransomware left behind for even a diligent malware analyst to discover and study.
That isn’t to say there aren’t artifacts and components to look at.
5/8
That isn’t to say there aren’t artifacts and components to look at.
5/8
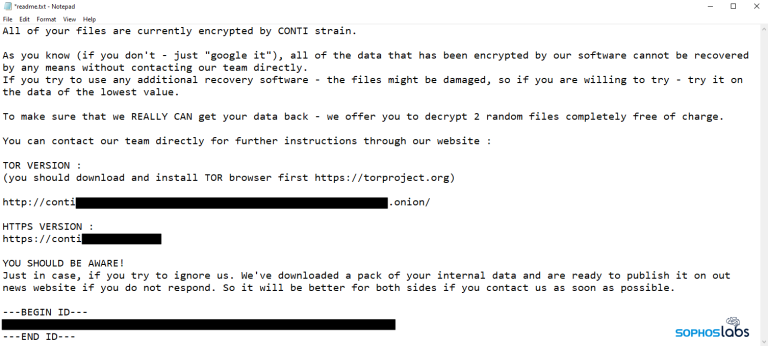
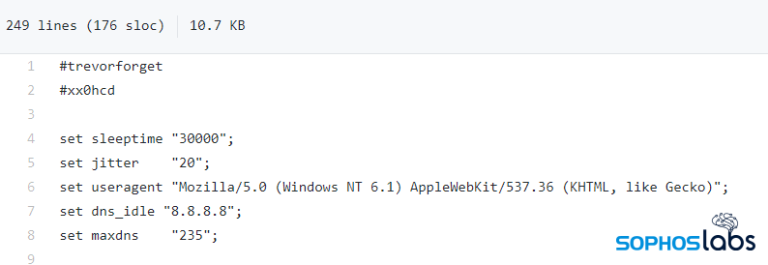
The threat actors involved in attacks using Conti have built a complex set of custom tooling designed not only to obfuscate the malware itself, when it gets delivered, but conceal the internet locations from which the attackers have been downloading it during attacks...
6/8
6/8
...and prevent researchers from obtaining a copy of the malware that way as well.
See the full report here: https://news.sophos.com/en-us/2021/02/16/conti-ransomware-evasive-by-nature/?cmp=30728
Indicators of compromise for malware samples examined in this research has been posted to the SophosLabs Github here: https://github.com/sophoslabs/IoCs/blob/master/Ransomware-Conti.csv
7/8
See the full report here: https://news.sophos.com/en-us/2021/02/16/conti-ransomware-evasive-by-nature/?cmp=30728
Indicators of compromise for malware samples examined in this research has been posted to the SophosLabs Github here: https://github.com/sophoslabs/IoCs/blob/master/Ransomware-Conti.csv
7/8
Many thanks to our researchers, Andrew Brandt @threatresearch and Anand Ajjan @AnandAjjan for their excellent reporting.
8/8
8/8

 Read on Twitter
Read on Twitter